You receive an email. It is from someone that you have exchanged some emails with, someone you know or someone that someone you know knows. It is an offer for a new project to check and price. You think “nice”! You press on the link, you go to a page that says “Microsoft OneDrive” or “Office 365”. It says, “to download the files please sign in”. You put your Office 365/Outlook password and you press download. You download something but you get a message, “Password Incorrect”. You try 2-3 times and then you give up. Or something is downloaded, you try to open it, and it says: “corrupted file”.
You contact the sender (if it happens to know them) and ask what file they have sent. They reply: “I haven’t sent any file. What email are you talking about?”. You explain but then you start realising…
You have been scammed
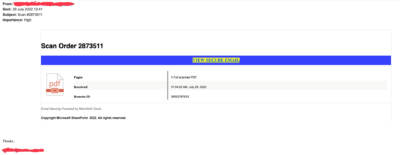
Every month I might receive 5-6 emails like the one in the picture below (blurred the sender as it was a real person that had their email compromised). At first glance, it seems a legit email. It’s coming from a legit account after all. But if you have received lots of them then you know the sender’s account has been compromised and the email is not coming from the sender.

If you open the link, you will be redirected to a new page. You might be tricked that this is a legit OneDrive or SharePoint (occasionally) web page. It prompts you to put you’re your Office/Outlook account credentials to download the file.
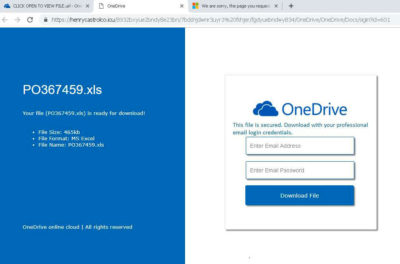
But take a closer look. The URL is not pointing to any OneDrive, SharePoint address (or any other known file sharing provider). What it is, is a copy of those pages and what it does is that: It collects your credentials.
Why it is very risky? Because the scammer has access to your email account. Your email account might have stored information that you don’t want to share, like personal emails, bank account access info, passwords, phone numbers etc.
What to do when you realise that you have been scammed? Change your password immediately and activate the two-factor authentication. Also, it would be nice if you could let the sender know that they sent a phishing email and that their account has been compromised.
How you can be protected from those phishing emails and how to recognise them?
First of all, the email looks a bit off. The text format is not constant, the fonts might be smaller of different between parts of the email.
It might be completely ok though. So secondly, you might press the link. This will lead you to a page that looks like the official Outlook, OneDrive, Dropbox etc pages. But the URL does not match. If you check the URL it will be something that you won’t understand or a page that is NOT the official page but probably will include the official name somewhere. Like: onedrivedownload.awebsite.com or anotherwsbsite.com/AJ34YPW09/dropbox. Those kinds of URLs are not official.

The official URLs would be something like outlook.com/whatever or dropbox.com/whatever. Thirdly, whoever wants to share files with you will use some services like WeTransfer, or the ones mentioned that WILL NEVER ASK ANY CREDENTIALS to download files. You will just receive a link, you will press it and the files will start downloading. Finally, to protect yourself from a phishing attack of this kind, it is better to use two-factor authentication. With this, even if you get scammed, the scammer cannot use your credentials to access your accounts because you will also have to put a code that you will receive with an SMS (the majority of the times) in a 2step process, besides your credentials.
Companies can also train their staff on cyber security. There are numerous courses out there that can be found if you google the term: “cyber security awareness training for companies”. It is interesting though that the UK Government has a training course portal as well, although it is not updated since 2019. You can find the page here.
One Extra Step – Making fun of the scammers
There are some more things you can do from here. One of those is to destroy the scammer’s database.
The concept is simple. The scammer’s page doesn’t have any security to check if you send too many requests to their endpoints. It is just a form to collect credentials that you put. So, one way to destroy their database is to inject 1000s of fake emails and passwords that look like real ones. This way, even if you have inserted real credentials it will be very difficult for them to recognise and check which ones are fake and which real. Of course, it is difficult and takes time to do it manually one by one.
For this reason, I created a script in Python (with the help of ChatGPT) that will do this job for me. If you are interested in this project take a look here!

